RSA's Products and Solutions
Security, Compliance and Risk-Management Solutions

RSA SecurID Suite
Modernizes your approach to secure access
RSA SecurID Suite enables organizations of all sizes to mitigate identity risk and maintain compliance without impeding user productivity. It ensures users have appropriate access and confirms they are who they say they are with a modern, convenient user experience. In addition, RSA SecurID Suite provides unified visibility and control across organizations’ many islands of identity.
Single Sign-on
- Maximize convenience while also minimizing points of vulnerability – users can sign on once for access to multiple resources
- Improve identity security by combining SSO with other identity and access management capabilities
Governance & Lifecycle
- A full-featured, high performing governance and lifecycle solution allowing you to focus on visibility, automate to reduce risk and maintain a sound compliance and regulatory posture
- Simplify access governance, streamline access requests and fulfillment, and provide a unified view of access across all of your systems and applications
RSA Hardware Authenticators
RSA ID Plus
ID Plus Subscription Plans
ID Plus offers three levels of cloud solutions, tailored to fit every identity and access management requirement. All of the solutions can be flexibly deployed in the cloud, on-premises, or hybrid with an open, extensible identity platform. The solutions also can be easily adjusted to meet the pace and evolution of your modernization.

ID Plus: DS100 Authenticator
The DS100 is a passwordless, multi-functional security solution that can dramatically enhance user experience while lowering total cost of ownership.
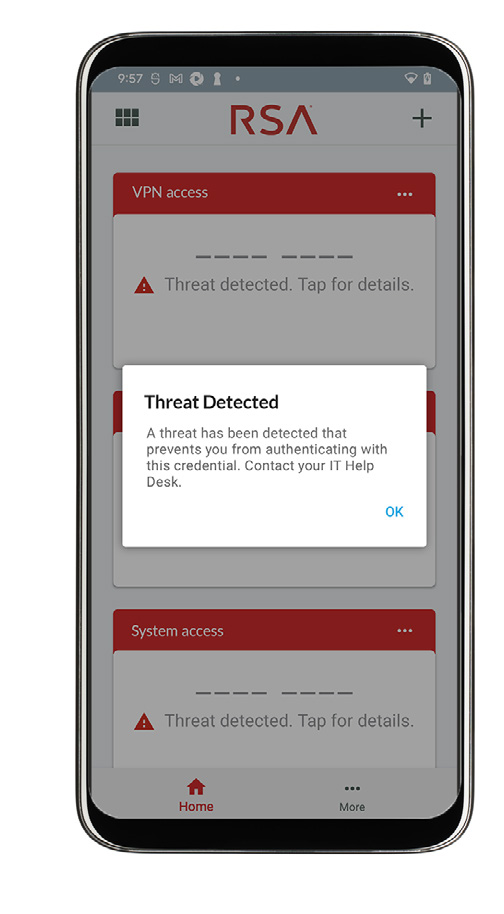
Mobile Lock
RSA Mobile Lock detects critical threats to a mobile device and restricts the user’s ability to authenticate until the threat issue is resolved, allowing IT to establish trust by verifying mobile devices across the attack surface, systematically protecting against threats, and securing any device to mitigate those threats.